Just like water finds a way, cyber criminals are constantly seeking cracks to seep through to obtain personal information that helps them steal money. “Phishing” is a known term to many that involves the sending of fraudulent emails with the hopes that a recipient will take the bait and divulge personal, identifying information to verify payment on a transaction. The next phase in the phishing evolution of cyber criminals is a term that might be new to you called “spear phishing”. This advanced phishing tactic initially made news in 2010 – 2011, but later research discovered that spear phishing was developed in the late 2000’s.
Spear phishing is a phishing method that targets specific individuals or groups within an organization. It is a potent variant of phishing, a malicious tactic that uses emails, social media, instant messaging, and other platforms to get users to divulge personal information or perform actions that cause network compromise, data loss, or financial loss. While phishing tactics may rely on shotgun methods that deliver mass emails to random individuals, spear phishing focuses on specific targets and involves prior research. It’s worth noting that by 2012, more than 90% of all phishing attacks were targeted spear phishing attacks.
What data is used to carry out a spear fishing attack?
Spear fishing falls under the “social engineering” category of cyber attacks, so the criminals will use public information about you to craft a message that’s tailored to your interests. These criminals can even analyze the trends of what types of emails you open and when you open them to be able to send you a fraudulent message when you’re most likely to open it. Some research says that spear phishing attacks target people in an organization that are responsible for company information, but the main takeaway is that these attacks are more acutely-crafted, and increased education is imperative.
What could a spear phishing message look like?
IBM’s “Cost of a Data Breach in 2022” report says that 55% of phishing attacks use brand names to make the message look legitimate. Some of the common company names being used are Amazon, Google, Netflix, and PayPal. Cyber criminals are even starting to create websites with “https” instead of “http” to make victims believe that the website they’re being asked to click through to is secure and trustworthy. 32% of all fraudulent websites use “https”.
Be wary of the standard requests for personal information like full name and date of birth, but also be wary of the sender. Is someone more likely to act on a fraudulent email if the message looks like it came from a senior employee, a colleague, or one of the trusted companies mentioned in the previous paragraph? Cyber criminals sure think so.
The tone of the message is also important to consider. Does the message have a sense of urgency, requiring you to immediately verify your information? A company does not contact you via email or phone to verify your information.
What is the impact of a phishing attack?
Of all cyber attacks, phishing attacks are the worst in terms of the combination of frequency and money lost. The average loss from a phishing attack is the highest at $4.91 million and has the 2nd highest breach rate at 16%. If that didn’t get your attention, what if you knew that the average phishing attack takes 219 days to identify and an additional 76 days to contain? Just 1 successful phishing attack can put many companies out of business.
Pro Tip from Security Title’s CTO, An-Shih Lee:
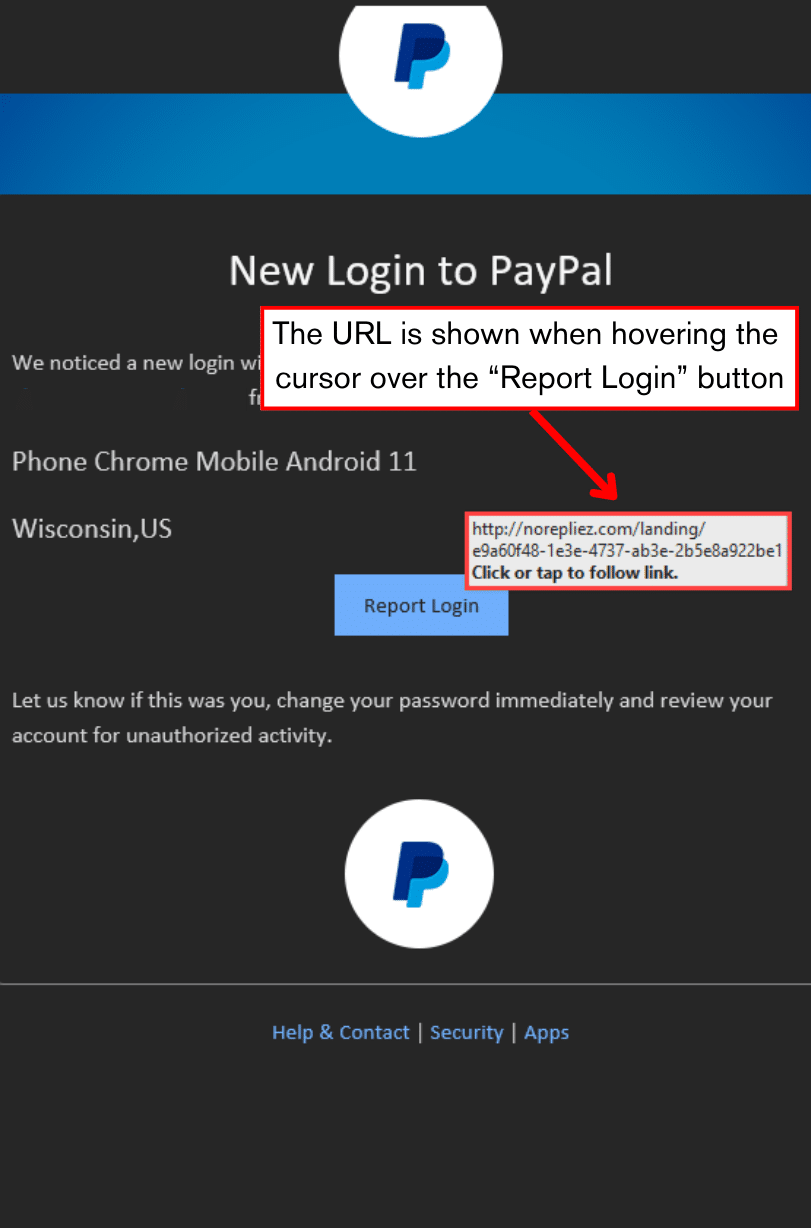
“If you hover your cursor over a link, or a button (aka image with hyperlink), your computer will show you the URL of where the link/button will take you. While this technique is not always 100% effective because the webpage can re-direct you elsewhere, it can be helpful in giving you more clues for your analysis of a potentially fraudulent message. Be careful not to actually click. Just hover the mouse cursor, wait a moment, and read.
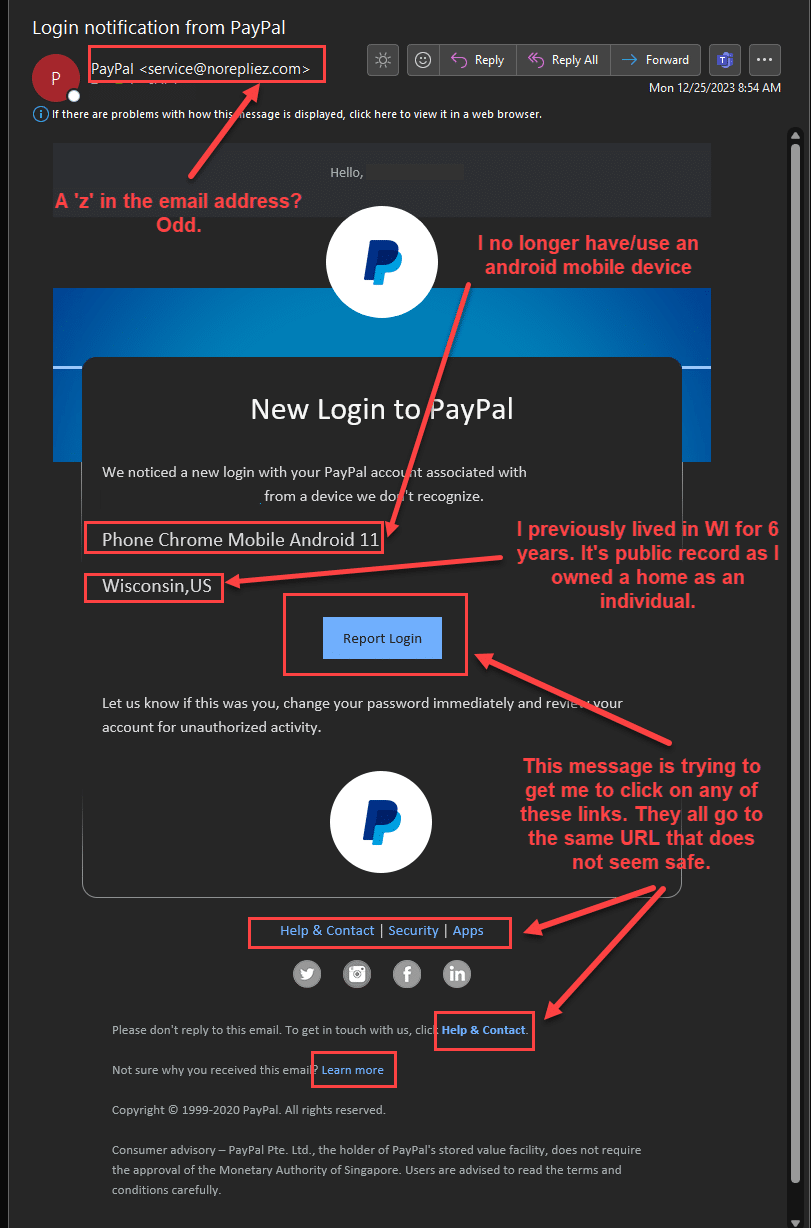
The 2 pictures below are from a real example of a spear fishing attack and the message utilizes some of the tactics covered in this blog. The criminal designed a message to look like it came from a trusted company in PayPal, then referenced public information like this recipient’s prior smartphone and the state where they previously lived. The recipient of this email was skeptical after a suspicious spelling in the email address, so they hovered their cursor over the hyperlinks without clicking. The URL showed the same suspicious spelling.”
The information about spear phishing in this blog merely dips a toe in the deep ocean of cyber crime, so please continue to educate yourselves on the constantly evolving tactics of cyber criminals because the losses can be devastating.
